Slmail 5.5 Serial Posted on 8/22/2018 by admin Seattle Lab Mail 5.5 POP3 Buffer Overflow There exists an unauthenticated buffer overflow vulnerability in the POP3 server of Seattle Lab Mail 5.5 when sending a password with excessive length. About Press Copyright Contact us Creators Advertise Developers Terms Privacy Policy & Safety How YouTube works Test new features Press Copyright Contact us Creators.
Description
There exists an unauthenticated buffer overflow vulnerability in the POP3 server of Seattle Lab Mail 5.5 when sending a password with excessive length. Successful exploitation should not crash either the service or the server; however, after initial use the port cannot be reused for successive exploitation until the service has been restarted. Consider using a command execution payload following the bind shell to restart the service if you need to reuse the same port. The overflow appears to occur in the debugging/error reporting section of the slmail.exe executable, and there are multiple offsets that will lead to successful exploitation. This exploit uses 2606, the offset that creates the smallest overall payload. The other offset is 4654. The return address is overwritten with a 'jmp esp' call from the application library SLMFC.DLL found in %SYSTEM%system32. This return address works against all version of Windows and service packs. The last modification date on the library is dated 06/02/99. Assuming that the code where the overflow occurs has not changed in some time, prior version of SLMail may also be vulnerable with this exploit. The author has not been able to acquire older versions of SLMail for testing purposes. Please let us know if you were able to get this exploit working against other SLMail versions.
Author(s)
- stinko <vinnie@metasploit.com>
Platform
Windows

Multiple buffer overflows in SLMail 5.1.0.4420 allows remote attackers to execute arbitrary code via (1) a long EHLO argument to slmail.exe, (2) a long XTRN argument to slmail.exe, (3) a long string to POPPASSWD, or (4) a long password to the POP3 server (CVE-2003-0264). Shouts to Mutts at #offsec
****************************************************************************
1. Fuzzing
We begin by fuzzing the application. It seems to crash at 'A'*2700.
***********************************************************
2. The Crash
When we view the program in Immunity we see it has crashed; EBP is overwritten, stack pointer points to a location in memory full of 'A', and EIP appears to be overwritten.
***********************************************************
3. POC Python Fuzz Script
Slmail 5.5 Serial Data
***********************************************************
4. Controlling EIP
We use pattern_create to generate a 2700-byte unique string to send to the application so we can determine the exact offset of characters that overwrite EIP.
***********************************************************
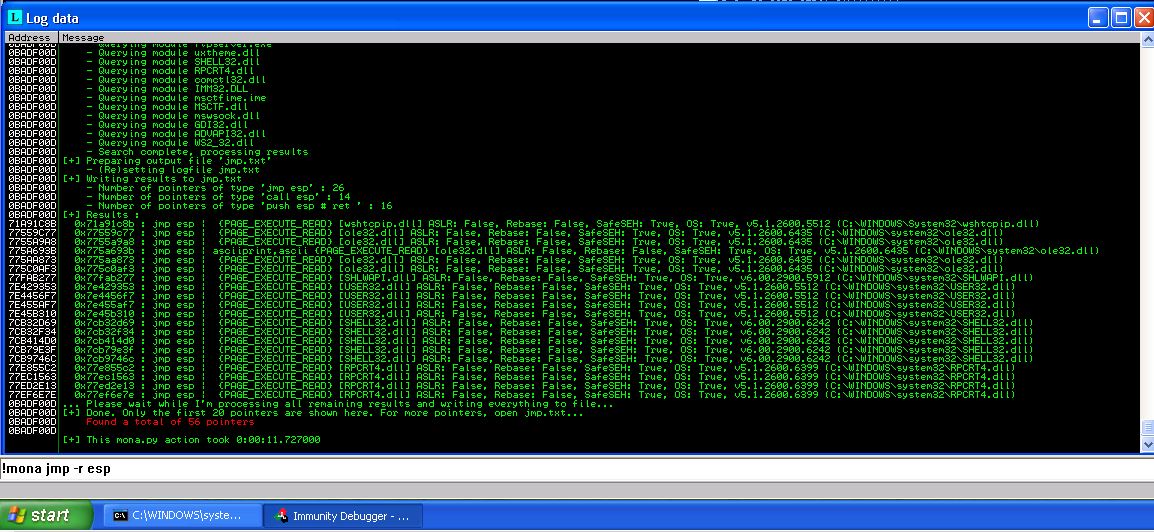
5. Redirect Execution Flow
Now we look for unprotected modules that were loaded with our application in order to ultimately find a JMP ESP instruction mnemonic if possible in order to jump flow control to the memory address where we will eventually place our shellcode.
***********************************************************


Slmail 5.5 Serial Killer
6. Exploit - EIP Redirect
After finding the memory address of a JMP ESP instruction in a loaded module, we update our script so that memory address put in EIP, and thus is the next address to which the program will go. Once there it will execute the JMP ESP and jump back to the ESP and the location in memory where we will place our shellcode.
The buffer: We know we need 'A'*2606 to get us right up to EIP, then we place the memory address of the JMP ESP command we found but in little endian format, then we calculate how much padding we need to place after increasing our buffer to 3500 bytes in order to overwrite a large block of memory to comfortably find a place for shellcode.
Slmail 5.5 Serial Key
****************************************************************************
7. Shellcode

All that's left to do now is to embed some shellcode into the script which will be placed in the 'C' buffer and executed after the JMP ESP is executed.
A simple TCP reverse shell created with msfvenom should work nicely.
****************************************************************************
Reference:
https://www.exploit-db.com/exploits/638/
http://www.securityfocus.com/bid/7519/discuss
https://www.exploit-db.com/exploits/646/
http://www.cvedetails.com/cve/cve-2003-0264